
Proactive Vulnerability Management for
Comprehensive Security
Identify, assess, and remediate vulnerabilities across your network with SecurityHive's integrated security platform
In today's dynamic threat landscape, understanding and managing vulnerabilities is crucial. SecurityHive's Vulnerability Management solution empowers your organization to stay ahead of potential threats by providing real-time insights and actionable guidance.
Trusted by companies around the world
Comprehensive Vulnerability Management
Our platform offers end-to-end Vulnerability Management, encompassing continuous discovery, risk assessment, and remediation guidance to fortify your security posture.
Continuous Discovery
Automatically scan your network to identify all assets and potential vulnerabilities.
- Automated Asset Discovery
- Comprehensive Network Scanning
- Supports Roaming Devices
Risk Assessment
Prioritize vulnerabilities based on their potential impact on your business.
- CVSS Scoring Integration
- Business Impact Analysis
- Exploit Probability Assessment
Remediation Guidance
Get actionable recommendations to fix vulnerabilities quickly.
- Easy-to-understand Solutions
- Risk Acceptance Management
- Automated Resolving Mechanism
Real-Time Insights and Reporting
Stay informed with real-time data and comprehensive reporting tools that facilitate informed decision-making and compliance readiness.




Tailored Solutions for Diverse Industries
SecurityHive's Vulnerability Management adapts to the unique security challenges of various industries, providing customized solutions to meet specific regulatory and operational requirements.
Financial Services
Protect sensitive financial data and meet strict compliance requirements for banks, insurance companies, and other financial organizations.
- Customer Data Protection
- Regulatory Compliance
- Third-party Risk Assessment
- Continuous Monitoring for Critical Assets
Healthcare
Safeguard patient data and medical systems with comprehensive Vulnerability Management designed specifically for healthcare providers and organizations.
- Patient Data Security
- Medical Device Security
- Operational Continuity
- Regulatory Compliance
Government
Secure critical infrastructure and sensitive government data with our Vulnerability Management platform.
- Critical Infrastructure Protection
- Policy Compliance
- Public Service Continuity
- Data Sovereignty Assurance
Manufacturing
Protect operational technology (OT) and IT environments with specialized Vulnerability Management for manufacturing and industrial organizations.
- OT/ICS Security Assessment
- Supply Chain Vulnerability Monitoring
- Equipment Lifecycle Management
- Minimal-Disruption Scanning
Retail
Secure e-commerce platforms, point-of-sale systems, and customer data with retail-focused vulnerability management.
- Compliance with PCI DSS Standards
- Point-of-Sale (POS) System Security
- Customer Data Protection
- Seasonal Risk Management
Technology
Integrate security into your development lifecycle with vulnerability management designed for technology companies and software developers.
- Application Security
- Infrastructure Resilience
- Intellectual Property Protection
- Compliance with Industry Standards
Security Research & Insights
At SecurityHive, we believe that informed organizations are better equipped to defend against cyber threats. Our dedicated research team continuously analyzes the evolving threat landscape to provide you with actionable insights.
Research Report
Threat Intelligence Updates
Stay informed about emerging threats and attack vectors with our regular updates, helping you to proactively adjust your security measures.
Webinar
Best Practices and Guidelines
Access expert recommendations and best practices to strengthen your organization's cybersecurity framework and compliance posture.
White Paper
In-Depth Vulnerability Analysis
Gain a deeper understanding of vulnerabilities, including their potential impact and mitigation strategies, through our comprehensive articles and reports.

Don't wait for hackers to down your network.
Catch them with Honey.
Try now. Cancel anytime.
How SecurityHive Works
Our comprehensive vulnerability management process helps you identify, prioritize, and remediate security risks.
1
Asset Discovery
Identify and inventory all assets across your network, cloud environments, and applications.
2
Vulnerability Scanning
Run comprehensive scans to detect vulnerabilities, misconfigurations, and security weaknesses.
3
Risk Assessment
Prioritize vulnerabilities based on severity, exploitability, and business impact.
4
Remediation Planning
Get actionable recommendations and guidance to address vulnerabilities.
5
Verification & Reporting
Verify that remediation efforts were successful and generate comprehensive reports.
Prepare for audits
Security is a continuous process. Our Vulnerability Management enables you to log the actions you take to solve vulnerabilities. It will also show when vulnerabilties were found or solved. Having an audit trail helps you in your next audit or when an incident occurs.

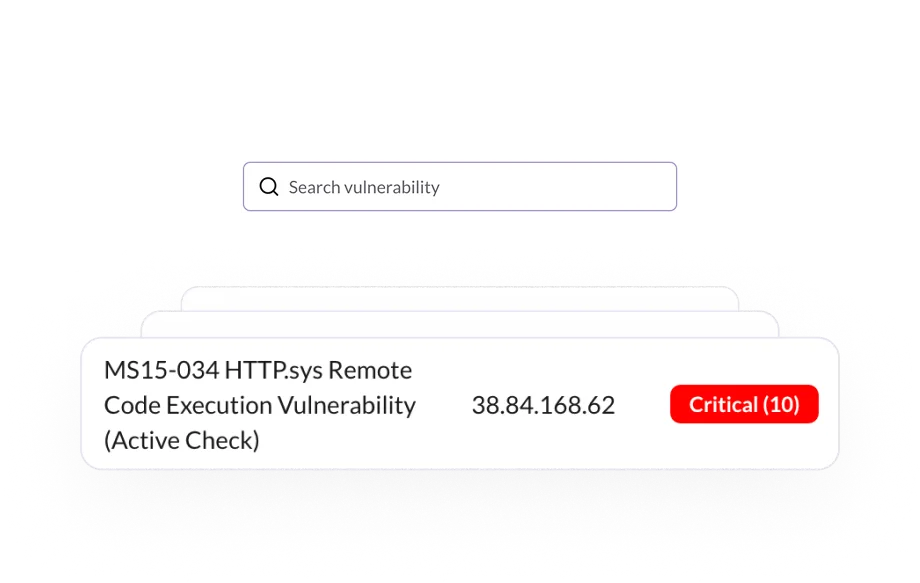
Internal Scan
Perform a scan on your internal network from network appliances to endpoints and more!
External Scan
Get to know how a hacker sees your network from the outside and discover how vulnerable you are.
Multi environment
Working in the cloud, having a traditional network or go hybrid? We scan all of them! Deploy easy and fast.
Policies
Scan and manage according to your company's policies. Let us help you to become compliant (e.g. ISO27001, BIO, custom).
Authenticated Scan
Vulnerabilities can exist on devices but may not be visible in your network. Scan your devices locally to detect these vulnerabilities.
Shadow IT
Discover all connected devices in your network including information like traceroutes, installed software, open ports and certificates.
Frequently Asked Questions
Get answers to common questions about our vulnerability management solution.
We recommend running vulnerability scans at least daily for critical systems and weekly for all other assets. However, the optimal frequency depends on your organization's risk profile, compliance requirements, and rate of change in your environment. SecurityHive allows you to schedule automated scans at whatever frequency best suits your needs. Our Agents offer near real-time scanning without the need to create a schedule.
Yes, SecurityHive is designed to integrate seamlessly with your existing security infrastructure. We offer pre-built integrations with popular SIEM solutions like Microsoft Sentinel, and ticketing systems like Datto Autotask PSA. Our API also allows for custom integrations with any tools specific to your environment.
SecurityHive uses a multi-factor approach to prioritize vulnerabilities. We consider the CVSS score, exploit availability, and exploit prediction scoring system. Our proprietary risk scoring algorithm helps you focus on the vulnerabilities that pose the greatest risk to your organization, rather than just those with high CVSS scores.
Absolutely. SecurityHive helps to become and/or stay compliant with major frameworks and regulations including PCI DSS, HIPAA, GDPR, ISO 27001, NIST, and more. Our platform helps you demonstrate due diligence during audits.
SecurityHive differentiates itself through its comprehensive approach that goes beyond simple scanning. Our platform also offers exceptional ease of use, requiring minimal configuration while delivering maximum visibility and control over your security posture.
Don't let hackers fool you. Fool them with our Honeypot.
Try now with our 14-day free trial. Are you able to evade our Honeypot? Easy setup within 15 minutes.





