Catch hackers with honey
What's the impact when a single door stays open? Our Honeypot solutions warns you when hackers entered your network. Don't let hackers roam around your network for months. Get alerted by the safety net of a Honeypot.
Trusted by companies around the world
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.

Common Problems Caused by Weak Network Security
In today’s hyperconnected world, even a small vulnerability can open the door to major breaches.
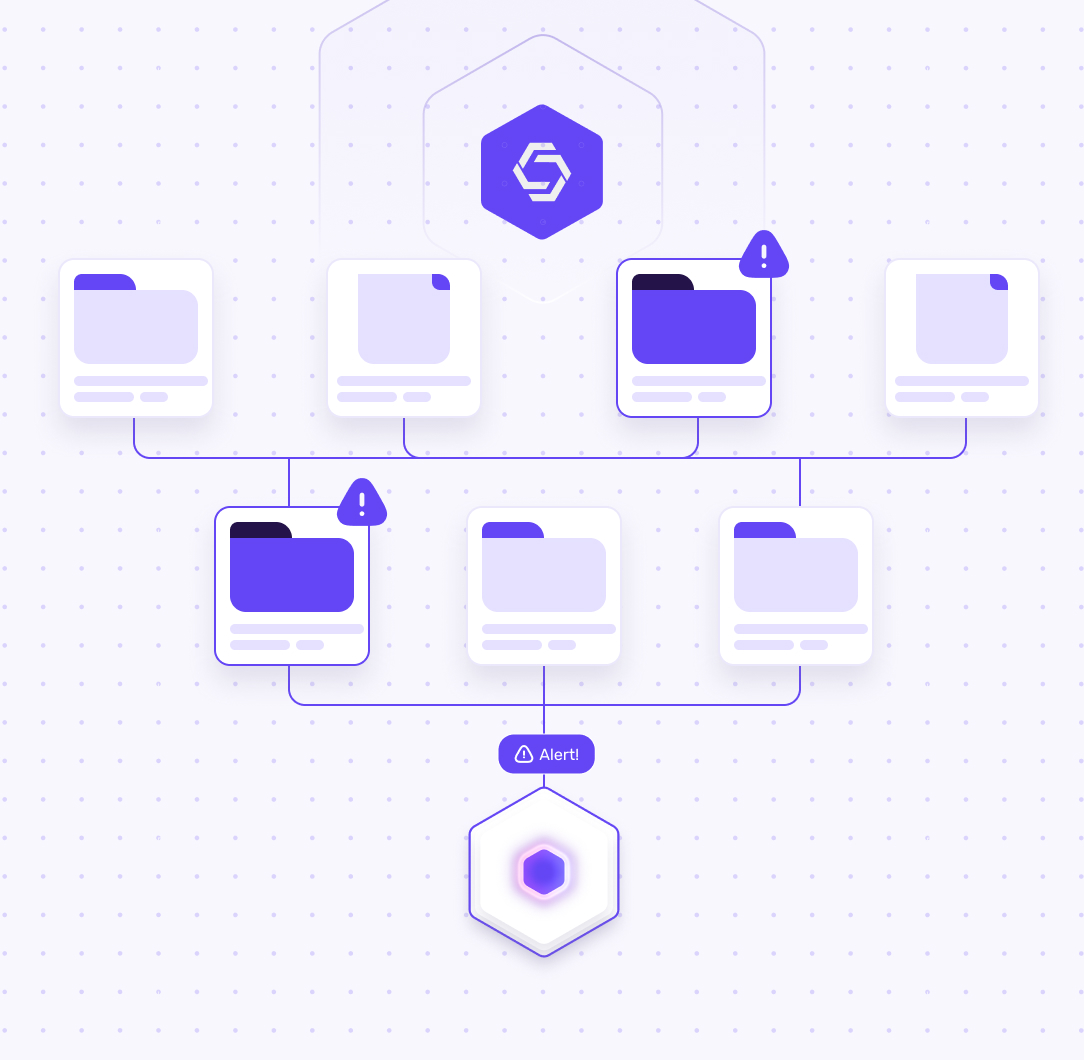
See east-west attacker movement
Traditional tools focus on perimeters and endpoints, leaving gaps between. Strategic honeypot placement illuminates internal traffic and lateral probing, revealing activity other controls can miss.
Spot intruders hours, not weeks
Attackers often lurk undetected. Honeypots act as early tripwires inside your network, surfacing reconnaissance and lateral movement quickly so you can contain incidents before damage spreads.
Reduce noise, raise signal quality
Security teams drown in low-value alerts. Honeypots only trigger when something’s off-path—so you get high-fidelity, low-volume alerts that highlight real threats, not routine ops noise.
Catch leaked or stolen logins
Planted decoy credentials and services expose adversaries who try reused or harvested accounts. Each interaction yields IOCs and behavior you can block or hunt across your environment.
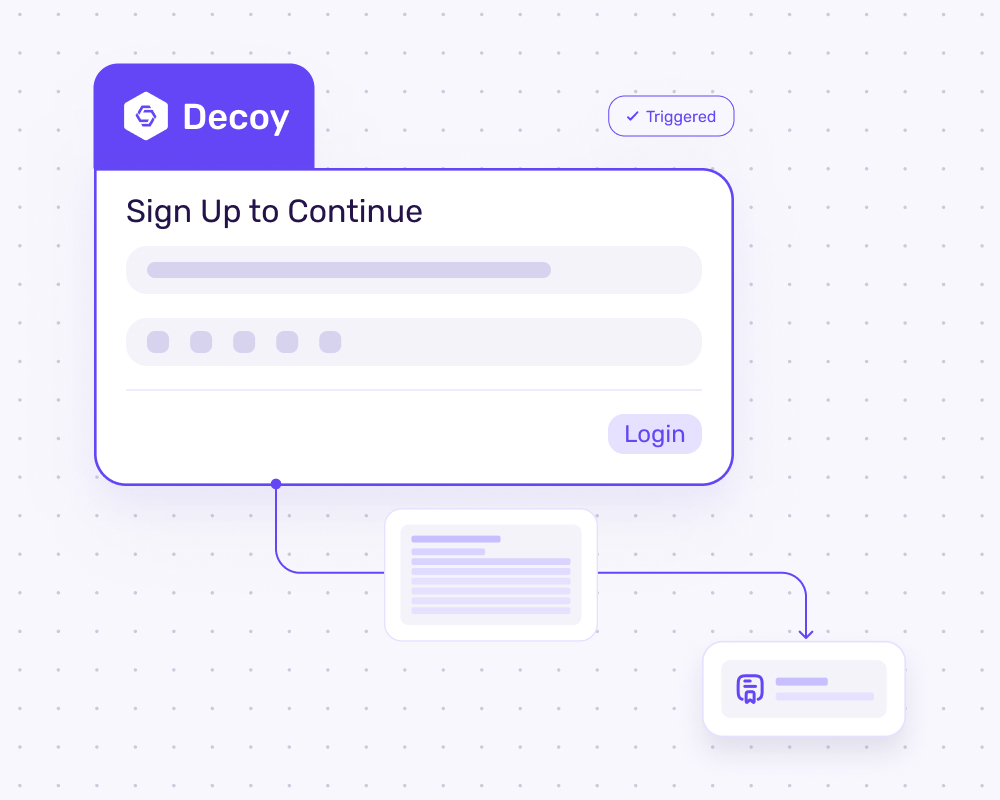
Detect staging and stop propagation
Before encryption starts, ransomware operators map shares and test execution. Honeypots mimic tempting assets, flag these stages early, and feed your SOAR to isolate hosts and cut blast radius.
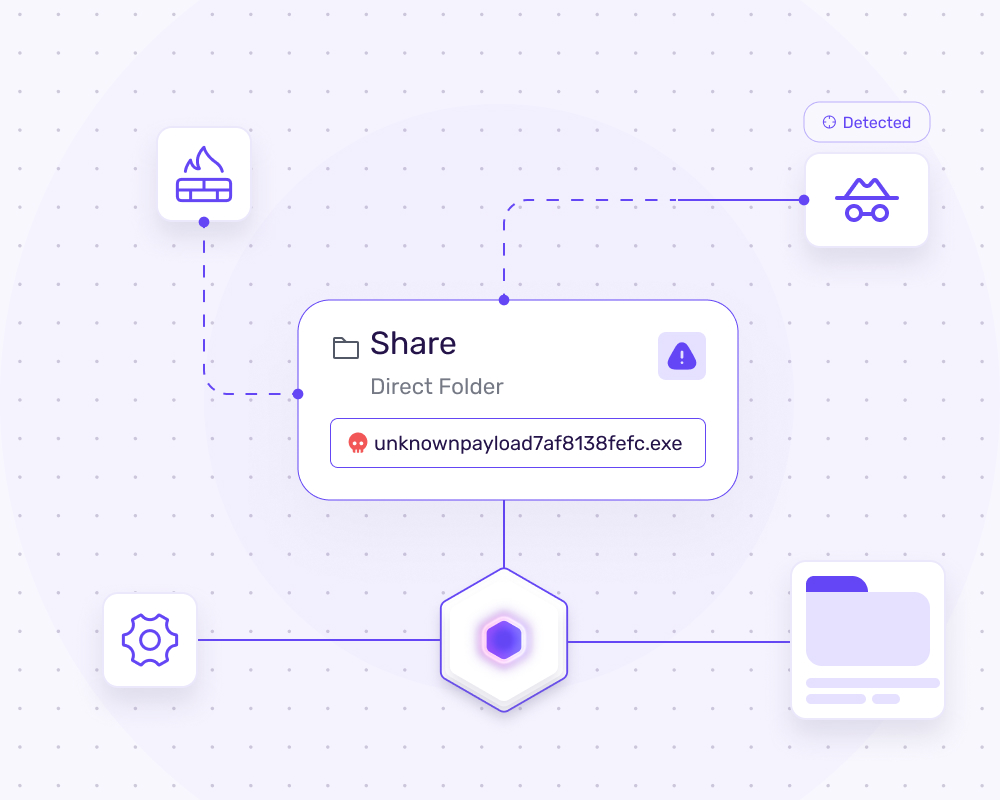
Detect & Distract
Hacker Detection detects hackers and distracts them to waste their time in a safe environment.
Alert
Get notified immediately when a hacker is detected so you can take measures.
Fingerprint
Track and identify hackers. Detect patterns and identify hackers across attacks.
Integrate
Integrate your monitoring system with our Hacker Detection to have full overview.
Credentials
Extract credentials used in attacks to improve your security and policies. Was it just a bruteforce attack or an old employee?
Evidence
Gather evidence for your insurance, law actions or police reports.
Create you free honeytoken
Digital tripwires that alert you when attakers access your systems.
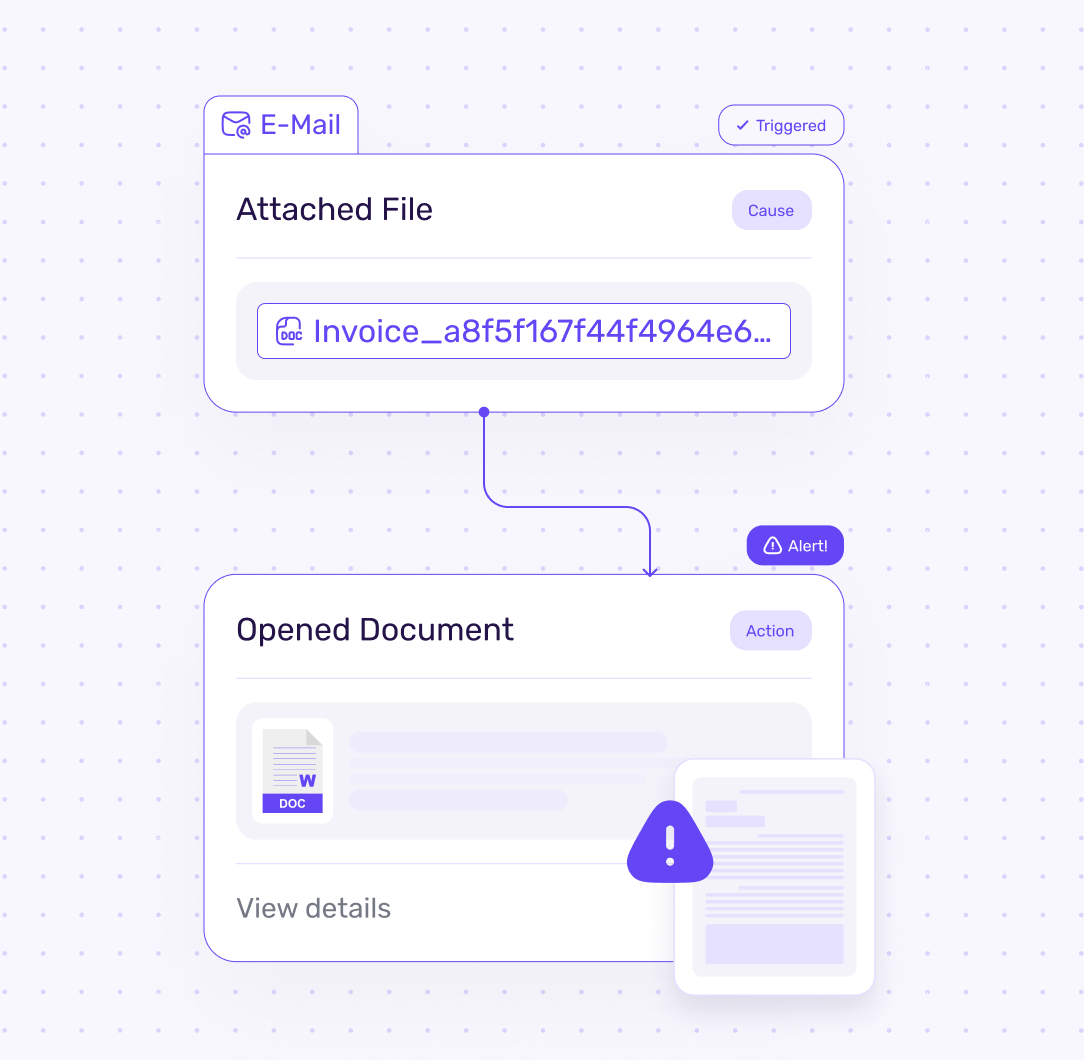
Word
Trap in documents
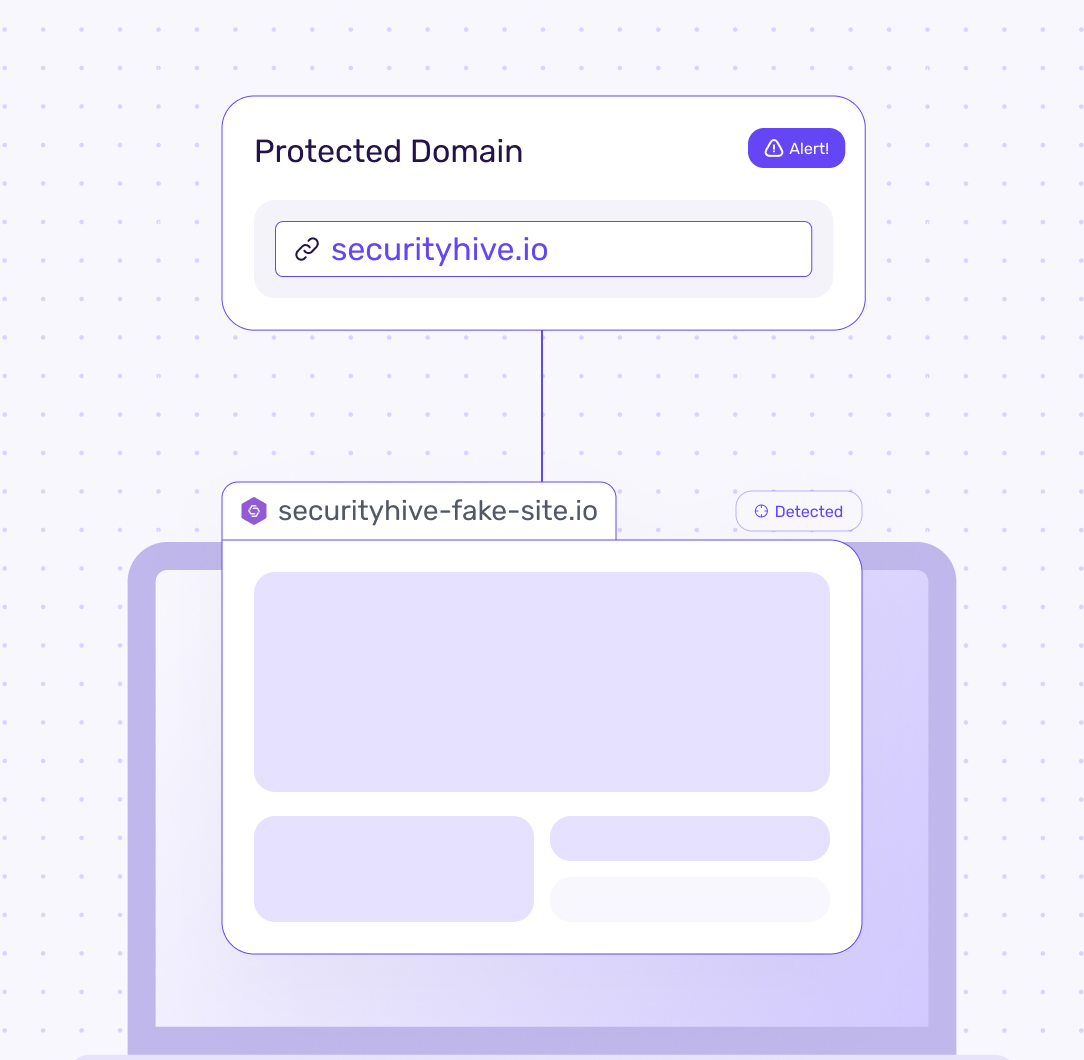
Embed in PDFs
SSH
Monitor Access
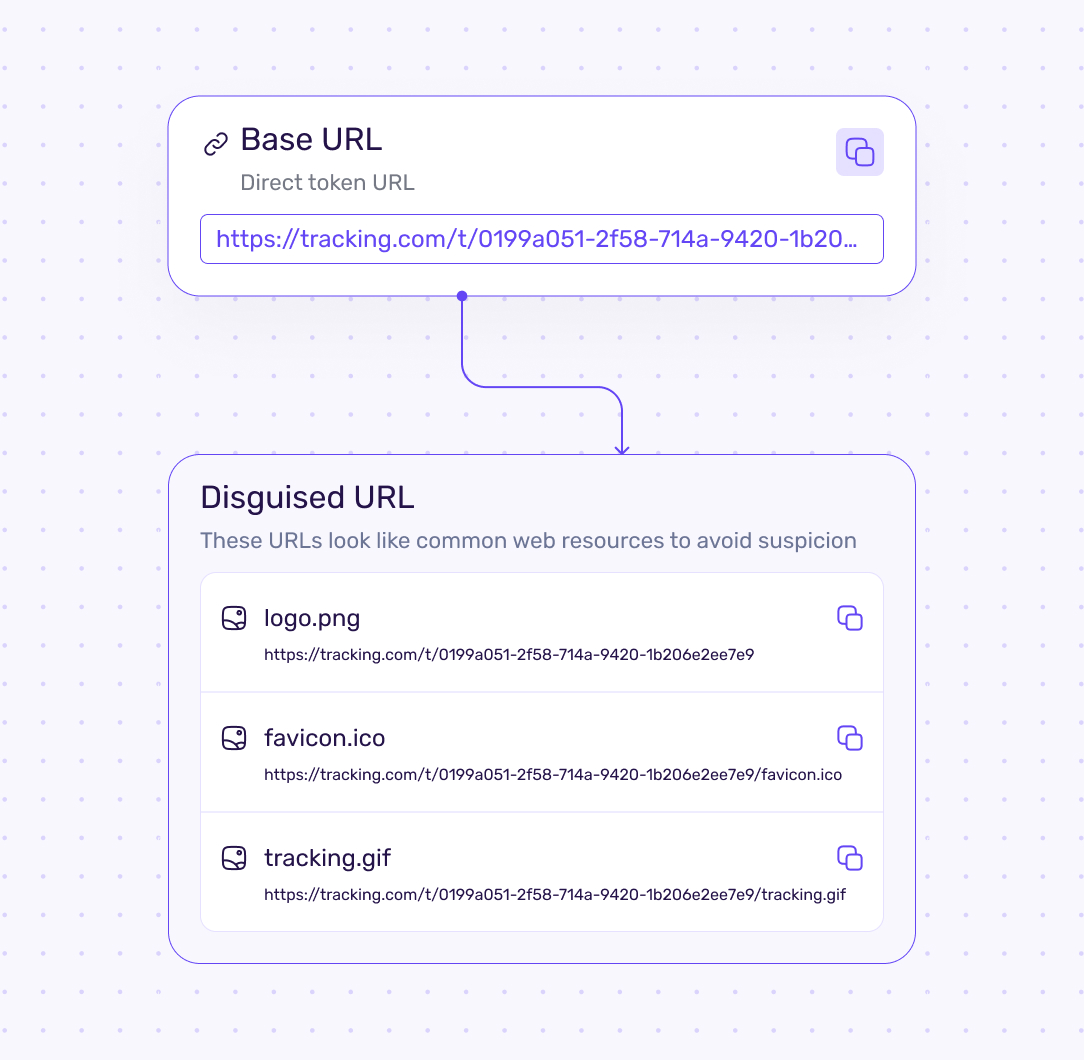
URL
Track Circles
How Honeypot helps you stay secure
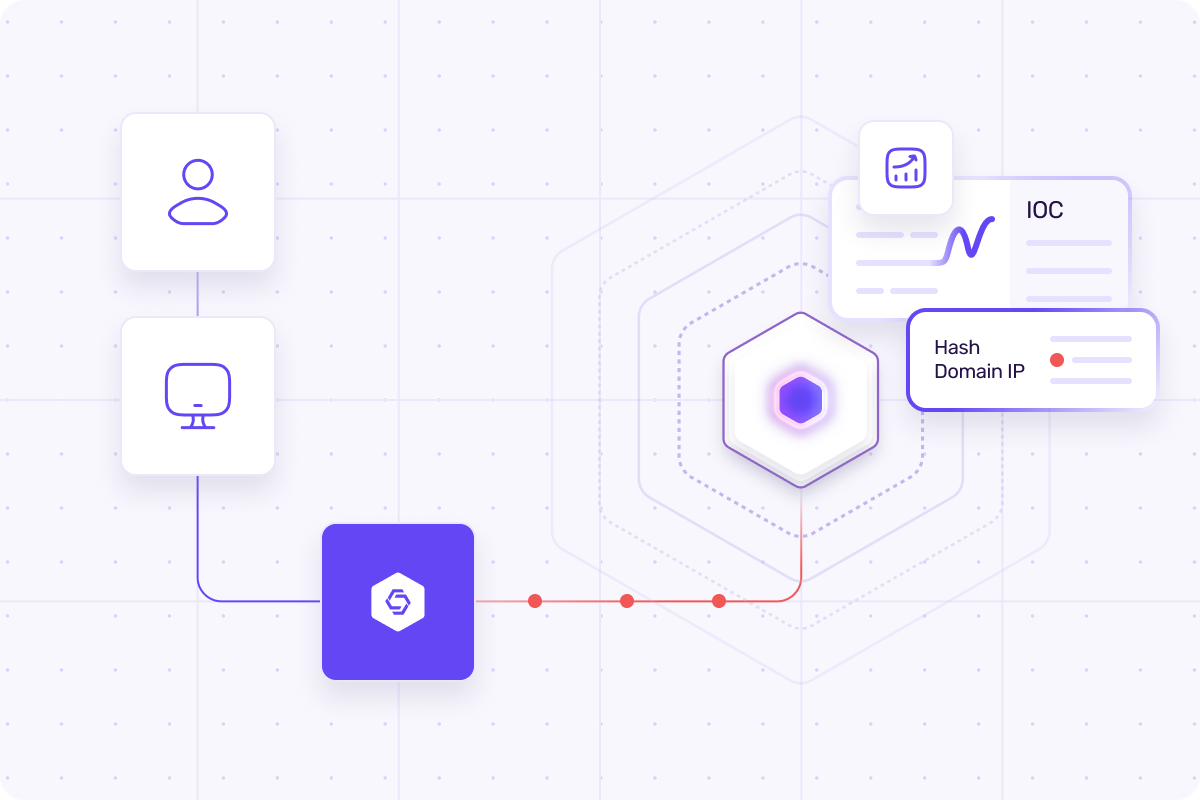
Understanding Attack Patterns
Insights into hackers' attack patterns. By analyzing their behavior and methods, you can better predict and prevent future attacks. This allows you to develop security measures that make your network even more secure.

Data Collection
Our smart sensors continuously collect data, enabling you to constantly optimize your security strategy. By staying one step ahead of hackers and continually improving your security based on the latest information, you enhance your defense.
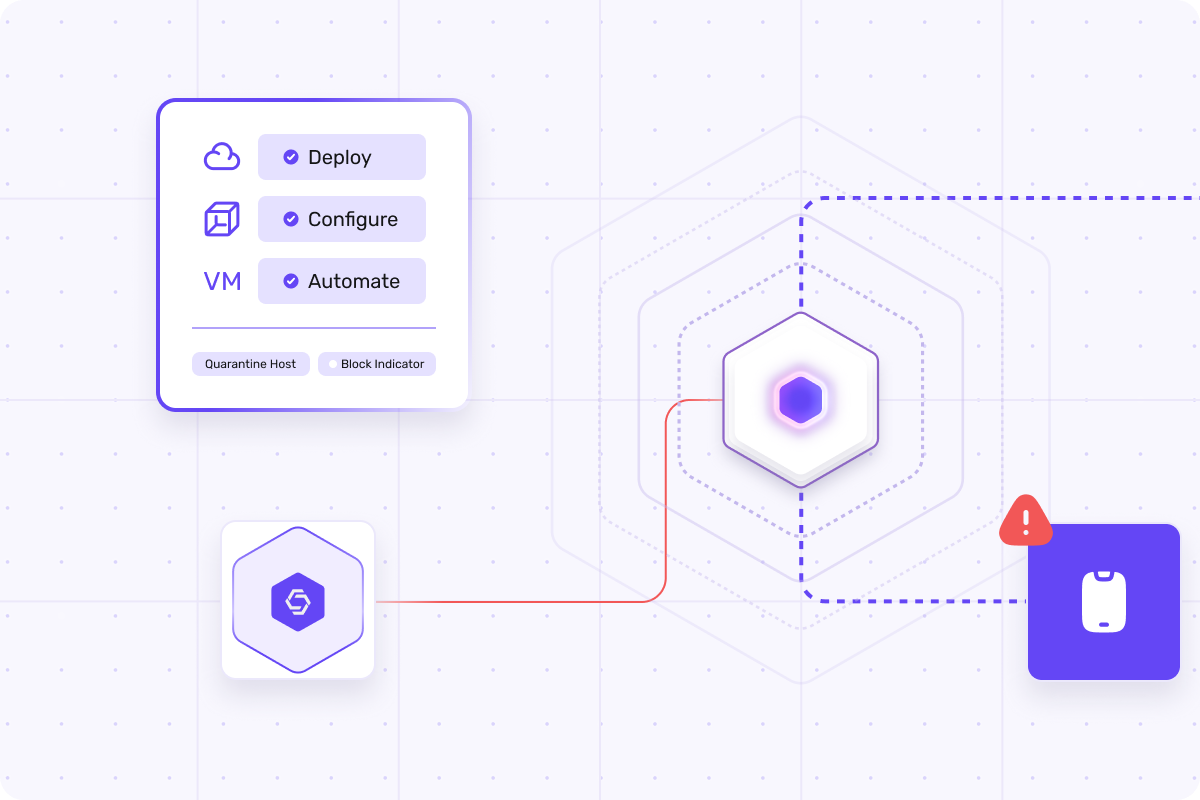
Easy Implementation and Management
SecurityHive's Honeypots are easy to implement and manage.Our user-friendly interface makes it simple to set up, monitor, and adjust your Honeypots. This allows you to fully focus on protecting your network without hassle.
Don't wait for hackers to down your network.
Try now. Cancel anytime.
Trusted performance backed by results
Honeypot that saves time, money, and risk.
< 000ms
from detection to alert
000 days
for hackers to go unnoticed
000%
100% simplicity. Deploy in minutes. Set up without complex integrations or overhead.
What Our Clients Are Saying
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.
Having a strong cybersecurity partner has been crucial in securing our community's information. Their tailored solutions ensure we stay compliant and resilient against cyber threats, giving us confidence in our ability to manage risks.
Working with SecurityHive has revolutionized our strategy. Their comprehensive solutions are specifically designed for local governments, allowing us to protect citizen data effectively and affordably.
Thanks to our cybersecurity solutions, we can focus on our mission instead of worrying about security breaches. The discounted rates for non-profits have been a huge help, and the team’s proactive approach genuinely cares about our safety.
The expertise we've gained from SecurityHive has been invaluable. Their tailored solutions fit seamlessly into our infrastructure, and with the educational discount, we've enhanced our security measures without breaking the bank.
Guidance in navigating complex compliance requirements has simplified our processes significantly. The tools we now use enhance our security posture while making reporting much easier, providing us with much-needed peace of mind.
The commitment to understanding our unique challenges sets SecurityHive apart. Their innovative solutions have fortified our defenses, allowing us to innovate without fear of cyber threats.
Partnering with a cybersecurity firm has been a game-changer for us. The proactive strategies in place have drastically reduced our risk profile, allowing us to focus on serving our clients without the constant worry of breaches.
The security solutions we implemented have transformed our approach to protecting sensitive patient data. Our team can now work with confidence, knowing we’re safeguarded against evolving threats.